Why Are AIOps Tools Essential For New Age Monitoring?

Blog Why Are AIOps Tools Essential For New Age Monitoring? Conventional monitoring provides the operations teams with critical visibility into the health of their IT systems with limited scope, but with the help of the AIOps tool, it allows the operations teams to significantly broaden their view. In a data center environment, multiple tools are […]
Identity & Access Governance – Is it a NEED or a WANT?
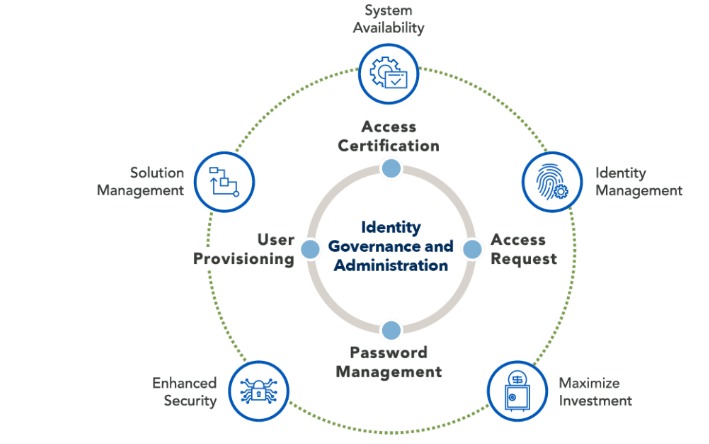
Blog Identity & Access Governance – Is it a NEED or a WANT? Identity Fraud Costs McKinsey estimates that synthetic identity fraud – in which criminals use fictitious IDs to secure credit is the fastest-growing type of financial crime in the United States. In the year 2016, synthetic identity fraud was responsible for up to […]
How to Realize Your File Requirements in Azure – Part 3

Blog How to Realize Your File Requirements in Azure – Part 3 High-Performance Computing – Challenges in the Cloud The cloud is effectively based on an agile pool of infrastructure resources – namely compute resources – that allows working environments to expand and contract as needed regardless of the size of the task at hand. […]
How to Realize Your File Requirements in Azure – Part 2

Blog How to Realize Your File Requirements in Azure – Part 2 Enterprise Database Applications – Challenges in the Cloud In order to meet mandates to get core application environments to the cloud, there comes the need to have a level of performance that is often difficult to achieve with today’s highly flexible cloud resources. […]
How to Realize Your File Requirements in Azure – Part 1

Blog How to Realize Your File Requirements in Azure – Part 1 An overview into how to solve challenges that moving to the cloud presents for file services, enterprise database applications, high-performance computing and analytics. As companies make the decision to transform IT operations by moving more of their applications1 to the cloud, they are […]
Protect Identities & Data – Elevate your Brand Value
Blog Protect Identities & Data – Elevate your Brand Value The average total cost of a data breach for the Middle East (KSA & UAE) is approximately 6.93 Million USD as per the IBM Cost of a breach Report (Aug 2021). Transitioning to remote work and a major emphasis towards cloud-first strategy is driving rapid […]
Microsoft New Commerce Experience (NCE)
Microsoft New Commerce Experience (NCE) What is the New Commerce Experience (NCE)? Microsoft has recently announced a change in how customers purchase and manage their licenses through their Cloud Solution Provider (CSP) Program. In January 2022, Microsoft launched New Commerce Experience (NCE). This change will impact the way you purchase Microsoft 365 licenses. But fear […]
Cloud Updates of the Week

Microsoft Azure had announced many new updates over the past week, out of which there were some important changes in SQL Server marketplace images and in Azure Bastion. We will see the changes and how they can help your organization in the Cloud Journey. SQL Server Images Microsoft Azure had recently made changes to the […]
Defining IT Security Audit

Blog Defining IT Security Audit IT Security Audits are performed to assess the confidentiality, integrity and availability (CIA) of an organizations information assets. The objective is to proactively create controls that would identify risks, provide recommendations, advice on mitigation strategy and finally enhance the security landscape. The intention of this write up is to define […]
Importance of “Going-Digital” During Remote Working and Beyond

Blog Importance of “Going-Digital” During Remote Working and Beyond Due to on-going pandemic, organisations have already adopted remote work, and looking to have specific functions executed remotely going forward. They have ensured business continuity by providing secure access to core systems outside the organisation network. Is this enough? Traditionally, employees had the option of walking […]
